While this is not something new, it perhaps has more significance because of the ever increasing market share of more than 60% of Chromium based browsers.
Chromium based browsers have a very uncanny method to check if the web browser is sitting behind a captive portal. And if you’re running a recursive resolver in your network with a large user base running Chromium based browsers (Google Chrome, Brave etc), it might even startle you if you observe the recursive resolver logs.
Here is a snippet from my unbound resolver as soon as I start Google Chrome on the machine(192.168.0.188),
Jun 3 11:16:31 root unbound: [1283:0] info: 192.168.0.188 pwpsfrn. A IN
Jun 3 11:16:31 root unbound: [1283:0] info: 192.168.0.188 yeytluindg. A IN
Jun 3 11:16:31 root unbound: [1283:0] info: 192.168.0.188 zkgtcrxrpfjcjxr. A INA research project at USC What’s In A Name? goes into some detail with the classification.
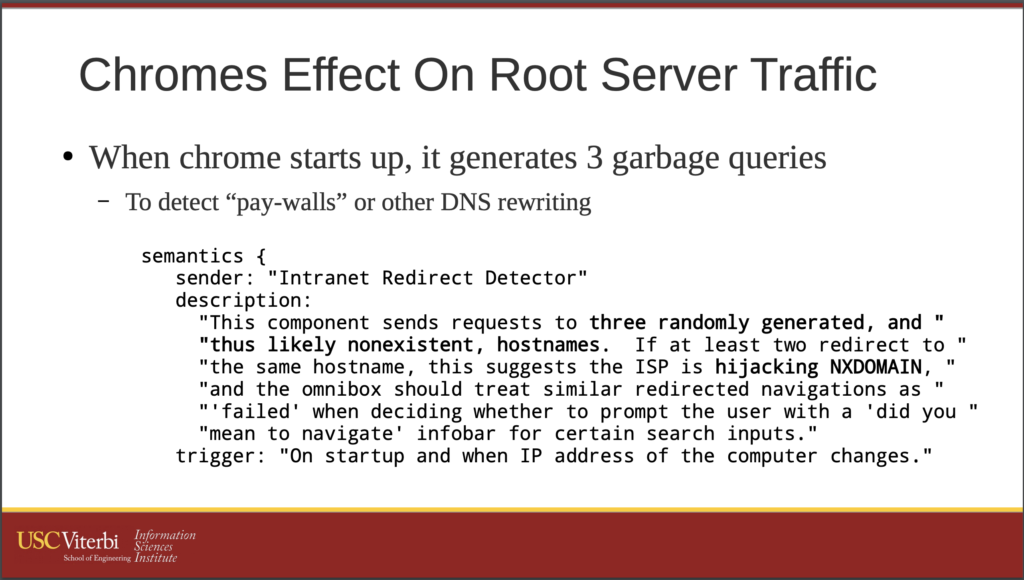
Here is the summary of the study,
Though the root server system handles this application-specific load sufficiently, it is clear that Chrome’s trick of using randomly generated names to discover whether it’s behind a captive portal contributes significantly to the traffic received at the root zone.
2 thoughts on “Chromium based browsers & DNS”