tl;dr If Jio VoWiFi isn’t working for you, set a different DNS resolver on the phone. While I am a big proponent of running your own resolver in the network, you could test by using open resolvers. The issue doesn’t seem to be impacting everyone and only a subset of users.
To begin with, there are multiple things broken in the authoritative name servers ns1.vowifi.jio.com. and ns2.vowifi.jio.com. of vowifi.jio.com which I’ll cover a bit later.
I came across reports ( See here & here ) of Jio VoWiFi not working for many and while the reports were sketchy, I decided to test this myself.
Below is a snippet from a log file of a dns query to vowifi.jio.com from my phone(192.168.1.137) to a recursive resolver(Unbound) which I run in my network,
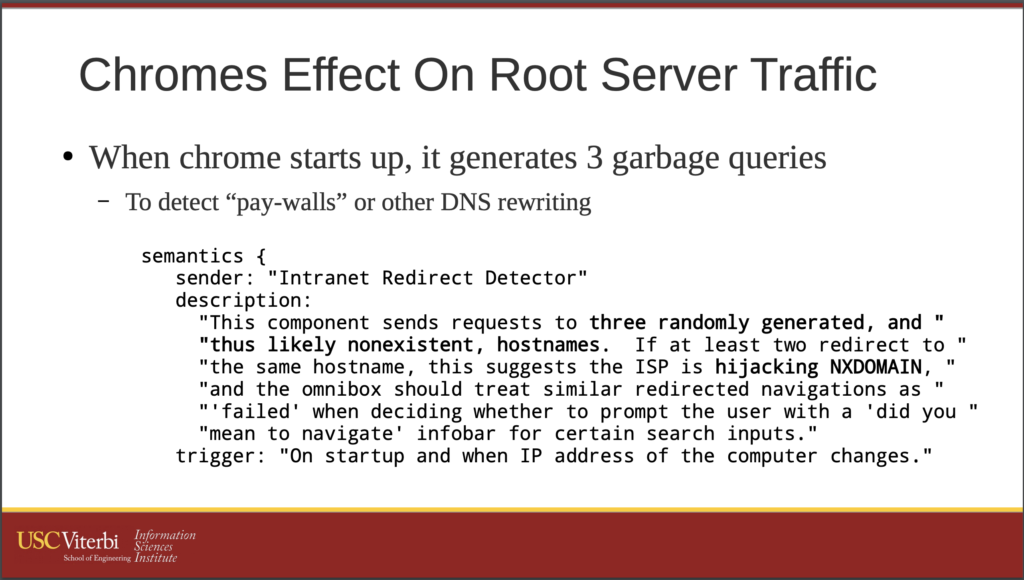
May 28 15:54:35 root unbound: [1300:0] info: 192.168.1.137 vowifi.jio.com. A INIdeally, the domain is standardised & is made up of Mobile Network Code(MNC) and Mobile Country Code(MCC). For example – in the case of Airtel VoWiFi, the domain name that I see hitting my Unbound resolver is epdg.epc.mnc045.mcc404.pub.3gppnetwork.org. where MNC – 045 and MCC – 404 which signifies Airtel – Karnataka region.
However, oddly enough, Reliance Jio seems to be using vowifi.jio.com. Having said that, the standardised domain name works as well. For example – epdg.epc.mnc861.mcc405.pub.3gppnetwork.org. resolves to 49.44.59.36 and 49.44.59.38
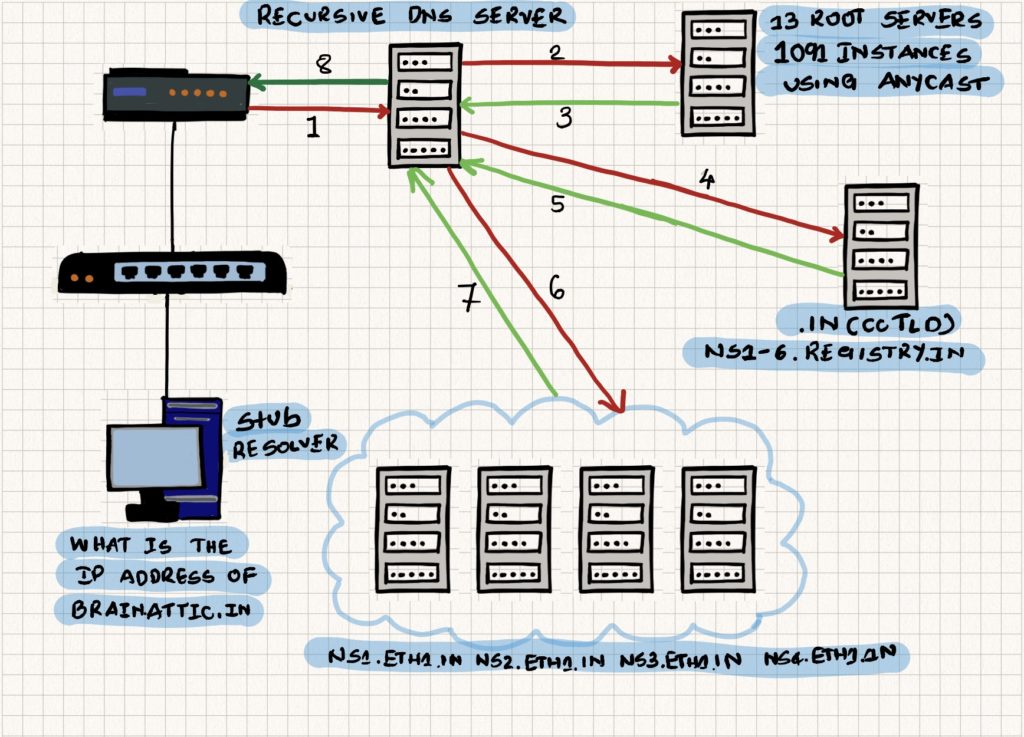
Below is the dns resolution entire delegation chain. From my home network, I can see that the vowifi.jio.com resolves to 49.44.59.38 and 49.44.59.36
. 518400 IN NS a.root-servers.net.
. 518400 IN NS b.root-servers.net.
. 518400 IN NS c.root-servers.net.
. 518400 IN NS d.root-servers.net.
. 518400 IN NS e.root-servers.net.
. 518400 IN NS f.root-servers.net.
. 518400 IN NS g.root-servers.net.
. 518400 IN NS h.root-servers.net.
. 518400 IN NS i.root-servers.net.
. 518400 IN NS j.root-servers.net.
. 518400 IN NS k.root-servers.net.
. 518400 IN NS l.root-servers.net.
. 518400 IN NS m.root-servers.net.
com. 172800 IN NS a.gtld-servers.net.
com. 172800 IN NS l.gtld-servers.net.
com. 172800 IN NS c.gtld-servers.net.
com. 172800 IN NS h.gtld-servers.net.
com. 172800 IN NS e.gtld-servers.net.
com. 172800 IN NS d.gtld-servers.net.
com. 172800 IN NS i.gtld-servers.net.
com. 172800 IN NS f.gtld-servers.net.
com. 172800 IN NS m.gtld-servers.net.
com. 172800 IN NS j.gtld-servers.net.
com. 172800 IN NS g.gtld-servers.net.
com. 172800 IN NS k.gtld-servers.net.
com. 172800 IN NS b.gtld-servers.net.
jio.com. 172800 IN NS ns1.jio.com.
jio.com. 172800 IN NS ns2.jio.com.
jio.com. 172800 IN NS ns3.jio.com.
jio.com. 172800 IN NS ns4.jio.com.
vowifi.jio.com. 3600 IN NS ns1.vowifi.jio.com.
vowifi.jio.com. 3600 IN NS ns2.vowifi.jio.com.
vowifi.jio.com. 5 IN A 49.44.59.38
vowifi.jio.com. 5 IN A 49.44.59.36At this point, I confirmed that VoWiFi on Jio works by putting the phone on Airplane mode while remain connected to WiFi. A ~22 minute call worked flawlessly.
To confirm that vowifi.jio.com was indeed the domain name that needs to resolve for VoWiFi to work on Jio, I configured an entry for vowifi.jio.com to return a NXDOMAIN answer in my DNS RPZ aka DNS Firewall in Unbound.
With that configured, any DNS query for vowifi.jio.com from any device in the network will be meted out with a NXDOMAIN answer. Below is a snippet from the Unbound log confirming the RPZ rule applied.
May 28 17:31:50 root unbound: [1191:0] info: 192.168.0.137 vowifi.jio.com. A IN
May 28 17:31:50 root unbound: [1191:0] info: RPZ applied [custom block to test vowifi] vowifi.jio.com. nxdomain 192.168.0.137@64521 vowifi.jio.com. A IN;; ->>HEADER<<- opcode: QUERY, rcode: NXDOMAIN, id: 14747
;; flags: qr aa rd ra ; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;; vowifi.jio.com. IN A
;; ANSWER SECTION:
;; AUTHORITY SECTION:
;; ADDITIONAL SECTION:
;; Query time: 136 msec
;; SERVER: 192.168.0.250
;; WHEN: Thu May 28 18:03:42 2020
;; MSG SIZE rcvd: 32And VoWiFi(Jio) stops working.
You can refer to the MNC and MCC codes list on Wikipedia – Mobile Network Codes in ITU region 4xx (Asia)
In the context of VoWiFi, the other noticeable problems with DNS infrastructure of Jio –
- A/AAAA records for ns1.vowifi.jio.com, ns2.vowifi.jio.com are missing
- ns1.vowifi.jio.com(49.44.59.6), ns2.vowifi.jio.com(49.44.59.7) don’t respond to queries over TCP
The other interesting thing that is worth observing is that when you try resolving vowifi.jio.com from outside India or use a DNS resolver which is perhaps not geographically located within India, the authoritative name servers ns1.vowifi.jio.com(49.44.59.6), ns2.vowifi.jio.com(49.44.59.7) give out a different set of IP addresses – 49.45.63.1, 49.45.63.2
; <<>> DiG 9.16.3 <<>> @127.0.0.1 vowifi.jio.com
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13728
;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;vowifi.jio.com. IN A
;; ANSWER SECTION:
vowifi.jio.com. 4 IN A 49.45.63.1
vowifi.jio.com. 4 IN A 49.45.63.2
;; Query time: 352 msec
;; SERVER: 127.0.0.1#53(127.0.0.1)
;; WHEN: Sat May 30 06:23:23 IST 2020
;; MSG SIZE rcvd: 75@varkey at IBF pointed out the OpenDNS Cache Check website which also seems to confirm it.
To confirm this hypothesis, I decided to utilise the RIPE Atlas probes to run a measurement. If you’re unaware of the RIPE Atlas project, check an earlier post – Host a RIPE Atlas software probe in your network.
And the results of the measurement are interesting. Out of the 75 probes which participated in the measurement, there were many probes which received the response 49.45.63.1 & 49.45.63.2 to the DNS query to vowifi.jio.com
| ASN | AS Name | DNS Response 1 | DNS Response 2 | Resolver IP address |
| 4758 | NICNET-VSNL-BOARDER-AP National Informatics Centre, IN’ | 49.45.63.2 | 49.45.63.1 | 164.100.3.1 |
| 4758 | NICNET-VSNL-BOARDER-AP National Informatics Centre, IN’ | 49.45.63.1 | 49.45.63.2 | 164.100.3.1 |
| 24186 | RAILTEL-AS-IN RailTel Corporation of India Ltd., Internet Service Provider, New Delhi, IN’ | 49.44.59.36 | 49.44.59.38 | 127.0.0.1 |
| 14061 | DIGITALOCEAN-ASN, US’ | 49.44.59.36 | 49.44.59.38 | 127.0.0.1 |
| 18209 | BEAMTELE-AS-AP Atria Convergence Technologies pvt ltd, IN’ | 49.44.59.38 | 49.44.59.36 | 202.53.8.8 |
| 18209 | BEAMTELE-AS-AP Atria Convergence Technologies pvt ltd, IN’ | 49.44.59.38 | 49.44.59.36 | 49.207.46.6 |
| 135190 | UBERCORE-AS Ubercore Data Labs Private Limited, IN’ | 49.45.63.1 | 49.45.63.2 | 192.168.1.200 |
| 135817 | ESTOB-AS-AP Esto Broadband Private Limited, IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.8.8 |
| 18207 | YOU-INDIA-AP YOU Broadband & Cable India Ltd., IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.8.8 |
| 134316 | WORLD-AS World Star Communication, IN’ | 49.44.59.38 | 49.44.59.36 | 1.1.1.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.0.1 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.44.59.36 | 49.44.59.38 | 10.98.0.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.1 |
| 17625 | BLAZENET-IN-AP BlazeNet_s Network, IN’ | 49.44.59.38 | 49.44.59.36 | 202.131.104.2 |
| 133661 | NETPLUS-AS Netplus Broadband Services Private Limited, IN’ | 49.45.63.1 | 49.45.63.2 | 192.168.1.2 |
| 133982 | EXCITEL-AS-IN Excitel Broadband Private Limited, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.1.1 |
| 133318 | MAXTECHA-AS Maxtech, IN’ | None | 49.44.59.38 | 192.168.1.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.36 | 49.44.59.38 | 1.1.1.1 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.45.63.2 | 49.45.63.1 | fd00:1:2:3::1 |
| 131442 | DIGITALNETWORK-IN Digital Network Associates Pvt Ltd, IN’ | 49.45.63.2 | 49.45.63.1 | 192.168.10.1 |
| 135260 | FOURTY2COMM-AS 42 Communications Pvt. Ltd., IN’ | None | 49.45.63.1 | 192.168.10.1 |
| 9430 | STPI-NOIDA Software Technology Parks of India,Block-IV, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.1.1 |
| 132933 | CTPLAND-AS CharotarTelelink Pvt Ltd, IN’ | 49.45.63.1 | 49.45.63.2 | 192.168.1.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.38 | 49.44.59.36 | 45.90.28.112 |
| 17488 | HATHWAY-NET-AP Hathway IP Over Cable Internet, IN’ | 49.44.59.36 | 49.44.59.38 | 202.88.152.8 |
| 55824 | NKN-CORE-NW NKN Core Network, IN’ | 49.45.63.1 | 49.45.63.2 | 200.200.200.7 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | None | 49.45.63.2 | 200.200.200.7 |
| 18196 | SEVENSTAR-AS Seven Star Internet Service Provider, IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.8.8 |
| 9829 | BSNL-NIB National Internet Backbone, IN’ | 49.45.63.1 | 49.45.63.2 | 2001:4860:4860::8888 |
| 134053 | EXPL-AS-IN ETHERNET XPRESS PVT. LTD., IN’ | 49.44.59.38 | 49.44.59.36 | fda9:ded9:2bc5::1 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.45.63.2 | 49.45.63.1 | 192.168.1.1 |
| 9829 | BSNL-NIB National Internet Backbone, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.1.1 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.45.63.1 | 49.45.63.2 | 10.0.0.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.38 | 49.44.59.36 | 202.56.215.55 |
| 55824 | NKN-CORE-NW NKN Core Network, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.7 |
| 17747 | SITINETWORS-IN-AP SITI NETWORKS LIMITED, IN’ | 49.45.63.1 | 49.45.63.2 | 172.22.146.1 |
| 134053 | EXPL-AS-IN ETHERNET XPRESS PVT. LTD., IN’ | 49.44.59.36 | 49.44.59.38 | 45.116.0.238 |
| 24186 | RAILTEL-AS-IN RailTel Corporation of India Ltd., Internet Service Provider, New Delhi, IN’ | 49.44.59.36 | 49.44.59.38 | 10.0.7.253 |
| 23860 | ALLIANCE-GATEWAY-AS-AP Alliance Broadband Services Pvt. Ltd., IN’ | 49.44.59.36 | 49.44.59.38 | 203.171.240.10 |
| 132215 | POWERGRID-IN Power Grid Corporation of India Limited, IN’ | 49.45.63.1 | 49.45.63.2 | 10.0.0.1 |
| 9498 | BBIL-AP BHARTI Airtel Ltd., IN’ | 49.45.63.2 | 49.45.63.1 | 192.168.0.44 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.1 |
| 17813 | MTNL-AP Mahanagar Telephone Nigam Limited, IN’ | 49.44.59.36 | 49.44.59.38 | 59.185.3.10 |
| 45528 | TIKONAIN-AS Tikona Infinet Ltd., IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.1 |
| 134325 | JETSPOTNETWORKSPVTLTD-AS JETSPOTNETWORKS PVT LTD, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.1.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.1.1 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.44.59.38 | 49.44.59.36 | 202.83.21.43 |
| 17747 | SITINETWORS-IN-AP SITI NETWORKS LIMITED, IN’ | 49.44.59.36 | 49.44.59.38 | 1.1.1.1 |
| 9829 | BSNL-NIB National Internet Backbone, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.1 |
| 134249 | MARGONW-AS Margo Networks Pvt Ltd, IN’ | 49.44.59.36 | 49.44.59.38 | 172.28.242.252 |
| 12222 | AKAMAI, US’ | 49.45.63.2 | 49.45.63.1 | 23.216.52.9 |
| 55836 | RELIANCEJIO-IN Reliance Jio Infocomm Limited, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.29.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.1.1 |
| 136336 | TICFIBER-AS Thamizhaga Internet Communications Private Limited, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.0.1 |
| 9829 | BSNL-NIB National Internet Backbone, IN’ | None | 49.44.59.36 | 192.168.0.1 |
| 55824 | NKN-CORE-NW NKN Core Network, IN’ | None | 49.44.59.36 | 192.168.0.1 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.36 | 49.44.59.38 | 125.22.47.125 |
| 55577 | BEAMTELE-AS-AP Atria Convergence Technologies pvt ltd, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.254 |
| 134326 | AIRDESIGNBROADCAST-AS Airdesign Broadcast Media Pvt Ltd, IN’ | 49.45.63.1 | 49.45.63.2 | 208.67.222.222 |
| 138786 | CCBSPL-AS-IN Crystal Clear Broadband Services Pvt. Ltd., IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.8.8 |
| 56166 | IISERBNET-IN IISER Bhopal Campus, IN’ | 49.44.59.38 | 49.44.59.36 | 172.30.1.2 |
| 24560 | AIRTELBROADBAND-AS-AP Bharti Airtel Ltd., Telemedia Services, IN’ | 49.44.59.38 | 49.44.59.36 | 192.168.1.1 |
| 9829 | BSNL-NIB National Internet Backbone, IN’ | 49.44.59.36 | 49.44.59.38 | fdf6:a86d:4264::1 |
| 55836 | RELIANCEJIO-IN Reliance Jio Infocomm Limited, IN’ | 49.44.59.36 | 49.44.59.38 | 192.168.31.1 |
| 139331 | DCORP-AS-AP DevelentCorp., IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.8.8 |
| 23860 | ALLIANCE-GATEWAY-AS-AP Alliance Broadband Services Pvt. Ltd., IN’ | 49.44.59.38 | 49.44.59.36 | 1.1.1.1 |
| 55836 | RELIANCEJIO-IN Reliance Jio Infocomm Limited, IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.4.4 |
| 17488 | HATHWAY-NET-AP Hathway IP Over Cable Internet, IN’ | 49.44.59.38 | 49.44.59.36 | 1.1.1.1 |
| 135718 | DISHAWAVESINFONET-AS DISHAWAVES INFONET PVT. LTD, IN’ | None | 49.44.59.36 | 1.1.1.1 |
| 4755 | TATACOMM-AS TATA Communications formerly VSNL is Leading ISP, IN’ | 49.45.63.1 | 49.45.63.2 | 8.8.8.8 |
| 16509 | AMAZON-02, US’ | 49.44.59.38 | 49.44.59.36 | ::1 |
| 15169 | GOOGLE, US’ | 49.45.63.1 | 49.45.63.2 | ::1 |
| 139331 | DCORP-AS-AP DevelentCorp., IN’ | 49.44.59.36 | 49.44.59.38 | ::1 |
| 24309 | CABLELITE-AS-AP Atria Convergence Technologies Pvt. Ltd. Broadband Internet Service Provider INDIA, IN’ | 49.45.63.2 | 49.45.63.1 | 192.168.1.10 |
| 9498 | BBIL-AP BHARTI Airtel Ltd., IN’ | 49.45.63.1 | 49.45.63.2 | 192.168.139.245 |
internationalvowifi.jio.com also seems to indicate VoWiFi International calling, which resolves to 49.44.59.36 and 49.44.59.38 from my vantage point. The same resolves to 49.45.63.1 and 49.45.63.2 from every location that I’ve managed to check from outside India.
Looking at the results, most likely the issue is with how ns1.vowifi.jio.com & ns2.vowifi.jio.com are responding to client subnet (EDNS0) in DNS queries.
Recommended reading
If you enjoyed reading this blog post, you might find root hints vs RFC 8806 interesting.