What is Little Snitch?
Little Snitch is a network monitor & application firewall for the Mac OS. On 21st May 2024, with the release of Little Snitch 6.0, a notable Blocklists feature has been made available.
While the ability to add a custom blocklist existed in prior versions, it was a manual step. Little Snitch 6.0 changes that. Little Snitch 6.0 now provides a prepopulated list of blocklists for blocking Advertising, Malware, Tracking, Gambling etc.


Considering that the StevenBlack hosts file is one of the premier list for blocking adware, I was surprised not to find the StevenBlack blocklist in the list.
The other nice addition to the list is URLhaus. At the time of writing, there were 183 malicious domain names in the list.

And, the lists auto-update,

What is the advantage of blocking using Little Snitch over a browser extension like uBlock Origin?
I use both the methods. But the method of using Little Snitch is more powerful because it covers access to network connections (adware/malware etc) from any process in the Operating System and not just from those made from within the browser.
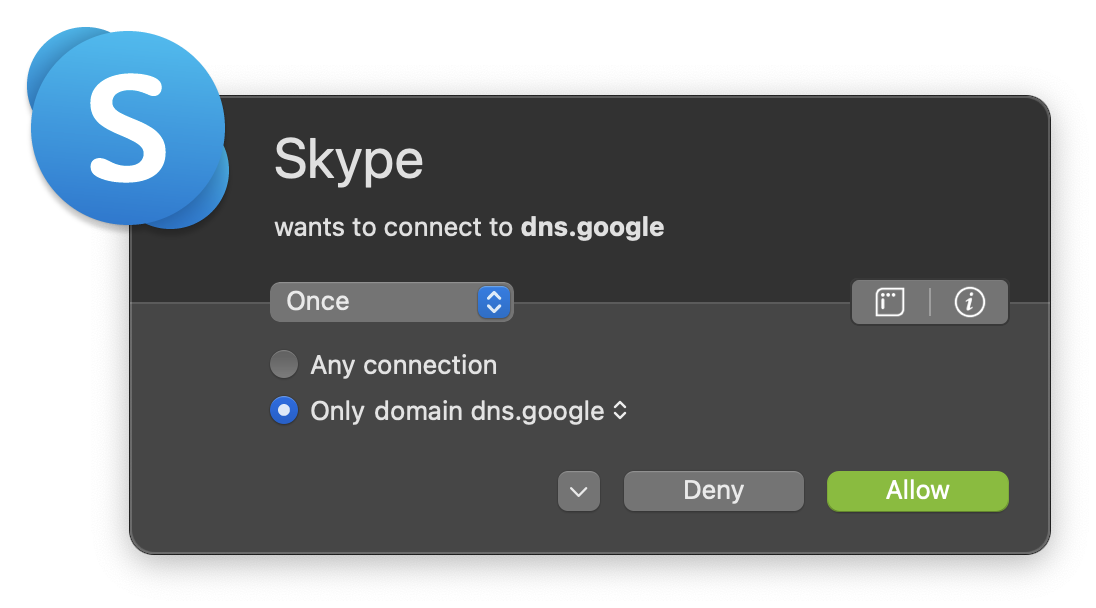
For example, Skype making a connecting to dns.google will be detected and can be blocked using Little Snitch.
It’s also important to note that this method of blocking network communication using an application firewall like Little Snitch might not scale if the blocklist is pretty large.
For example, the newly registered domain names dataset will most definitely cause the application to misbehave. In such cases, nothing beats having protection by using a DNS Firewall/DNS RPZ (Protective DNS).
Open Snitch for GNU/Linux
On similar lines to Little Snitch, Open Snitch is a GNU/Linux application firewall. Though I have to mention that I haven’t tried it yet.
Little Snitch can also be used to capture network traffic of a specific process.
Recommended reading
If you enjoyed reading this blog post, you might find root hints vs RFC 8806 interesting.