If you have never heard of the addon Firefox Multi Account Containers, this blog post is for you.
Isolation of websites, logins or identities
The addon is a must-have if you’d like to compartmentalize websites/logins or identities. Isolation is a critical component not just for OpSec but also for preventing surveillance on the Internet. While this addon won’t stop all tracking methods such as canvas fingerprinting, that use Javascript, it’s a good first in isolation.
Under the hood, it separates website storage into tab-specific Containers. Cookies downloaded by one Container are not available to other Containers.
https://addons.mozilla.org/en-US/firefox/addon/multi-account-containers
One way I tend to use it is to assign a website to a container. For example – https://youtube.com would go in a container “Youtube, any work-related websites would go inside a container “Work”, and my bank website would go in a separate container. This makes using Firefox Multi Account Containers very effective.
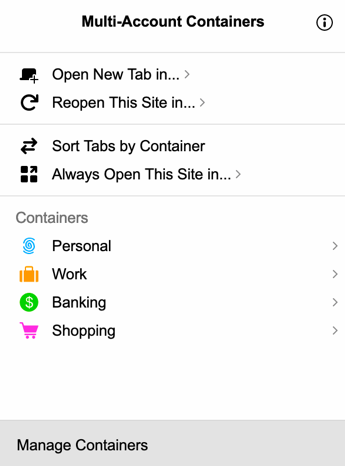
Figure 1: Image of the Firefox Multi account containers
The other benefit of the addon is the ability to login into two separate identities for example gmail.com email accounts in two separate containers. Why is this better than say using a Private window in Firefox or Incognito Window in Chrome?
From a usability perspective, both, Private Window and Incognito Window open a new Window. In comparison, the addon blends into the existing window but provides the additional feature of isolation of cookies, storage etc.
Most importantly, the addon prevents CSRF and clickjacking attacks by utilizing Firefox Multi Account Containers.
The full documentation of the addon is available here and here.
Recommended reading
If you liked this blog post, you might also enjoy reading Little Snitch Blocklists